 Norman Nie of Stanford University says, "You can't get a hug or a kiss over the Internet." (Social Intelligence: The New Science of Human Relationships, p. 9).
Norman Nie of Stanford University says, "You can't get a hug or a kiss over the Internet." (Social Intelligence: The New Science of Human Relationships, p. 9).Daniel Goleman, the author of the 1995 best-seller Emotional Intelligence, has authored a new book which I hope every IT Manager makes time to read, Social intelligence. The point of the book is that we are all "wired to connect", no matter how much technology is part of our everyday experience. In fact, in the beginning of the book, it is clear that Goleman believes recent technological developments are insulating most of us from that essential human connectivity for which we are biologically wired. From the car, to the cell phone, to the iPod, Goleman argues we are encasing ourselves in technology which isolates us from one another, leading to what he calls social autism.
Stephen Covey made a similar point in his book First Things First (1996) when he said, "You can be efficient with things, but you need to be effective with people, particularly on jugular issues." I've remembered that point over the years, but it bears repetition. With Goleman's new book, not only is the point repeated, it is reinforced with research from the the new discipline of social neuroscience. Our emotions and moods are all about human connectivity and the jugular issues of communication.
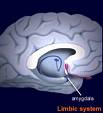
In the opening chapters, for instance, he talks metaphorically about the high road and the low road of communication. The high road is all about the frontal lobe of the brain, the location where reflection and rationality intercede, hopefully stopping us from saying something stupid. The low road, on the other hand, is all about the amygdala, almond-shaped groups of neurons buried deep within the temporal lobes of the brain where we sense one another's mood and emotions before we have had time to reflect or rationalize. The salient point is that the low road works far, far faster than the high road.
We experience this whenever we watch a movie or are engaged in a conversation with someone and intuit something going on. Whenever there is a hint of a smile on someone's face and we respond with our own smile or, even in a more subtle fashion, with a minor shift in mood which mirrors that of our conversationalist. All of this happens in an instant and before we are aware of what is going on consciously. This means, of course, that there is far too much information in one-on-one conversation to rely on e-mail, instant messaging, blogs, or other forms of communication which technophiles, like IT managers, use and promote everyday.
We may not hug or kiss one another in such conversations, but the point is still valid. The wiring we use for our technology cannot, and perhaps never will be, as effective in communicating with one another as the face-first conversation.